Remote Access 模式, 簡單地說, 就是使用一般的 PC 上面的 VPN Client 軟體, 接入總公司的VPN閘道器.
VPN 閘道器端設定摘要如下:
1. 定義 "封包保護套餐" (Transform Sets)
!
crypto ipsec transform-set CLIENT-SET esp-aes 256 esp-sha-hmac
!2. 定義 "群組設定值, 和帳號密碼驗證方式與授權" (Group Client Configuration, Authentication and Authorization for ISAKMP)
!
aaa new-model
aaa authentication login AAA-AUTHENTICATION local
aaa authorization network AAA-AUTHORIZATION local
!
username User101 password 0 Password101
username User102 password 0 Password102
username User103 password 0 Password103
!
crypto isakmp client configuration group ALL-CLIENTS-GROUP
key vpngrouppassword
pool CLIENT-ADDRESS-POOL
!
crypto map REMOTE-ACCESS-MAP client authentication list AAA-AUTHENTICATION
crypto map REMOTE-ACCESS-MAP isakmp authorization list AAA-AUTHORIZATION
crypto map REMOTE-ACCESS-MAP client configuration address respond
!
ip local pool CLIENT-ADDRESS-POOL 10.100.1.1 10.100.1.10
!3. 定義 "封包保護機制腳本" (IPSec Crypto Map)
!
crypto dynamic-map DYNAMIC-CONFIG-MAP 10
set transform-set CLIENT-SET
!
crypto map REMOTE-ACCESS-MAP 10 ipsec-isakmp dynamic DYNAMIC-CONFIG-MAP
!4. 定義 "VPN閘道器間交談過程" 的保護加密機制 (ISAKMP policy)
!
crypto isakmp policy 100
encr aes 256
authentication pre-share
group 5
!5. 啟用 "封包保護機制腳本" 在網路卡上
!
interface Serial0/0/0
ip address 172.16.1.1 255.255.255.252
crypto map REMOTE-ACCESS-MAP
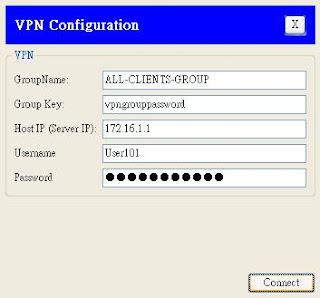
!Client PC 端設定
先使用 User101 這個帳號為例: 參數請參照前面設定黃色的部份.
GroupName: ALL-CLIENTS-GROUP
Group Key: vpngrouppassword
Host IP (Server IP): 172.16.1.1
Username: User101
Password: Password101
(其實本例中另外定義 User102, User103兩帳號, 密碼分別是 Password102 和 Password103, 都可以試看看!)
登入畫面擷取如下圖示:
登入成功:
登入成功後, 顯示所取得的 VPN 內部的 IP 位址:







0 意見:
張貼留言
小技巧:也可以 匿名 留言!